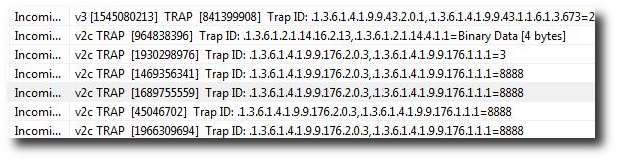
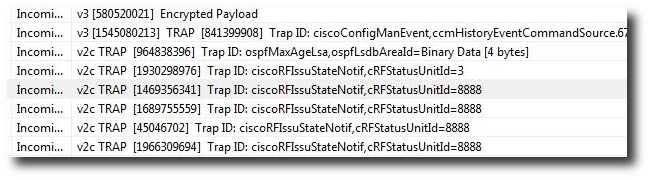
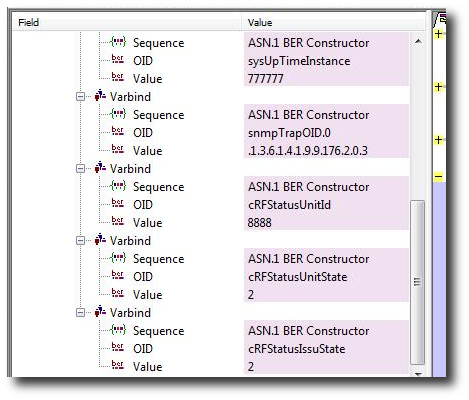
Who says people who look at raw packets cant have fun ? Let’s see how we can reconstruct YouTube videos from raw packets and play them back directly from Unsniff. We also show you a nifty Ruby script to automate this.
Playback
1. Fire up Unsniff Network Analyzer and start a packet capture
2. Go watch some YouTube video(s) to completion. We will explain how to deal with half played videos later.
3. Once you are done, switch over to the User Objects tab where all the action is. You will see a list of “user objects” extracted by Unsniff from the stream. Click on the Type column to sort by Type and locate the FLV objects. Right click to Save or Play (To playback you need the free VLC Player installed and FLV files associated with VLC).
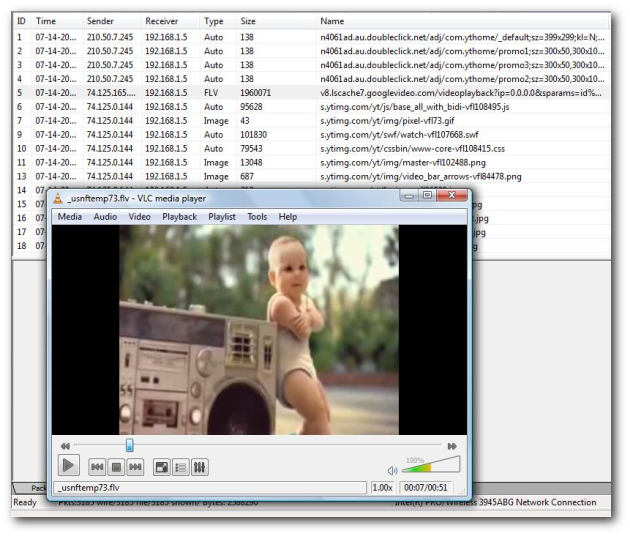
Feeling adventurous ? Lets try some more tricks.
Pruning the packet capture
When you interact with a site like YouTube there is a ton of content exchanged, not all of it is the video bits. You have packets containing images, HTML, Flash, and Javascript. The actual FLV is exchanged in a single TCP stream. If you can save these streams alone, you will be able to reconstruct the videos.
Here is how you do it.
1. Switch over to the “Sessions”, here is where you will see a list of TCP sessions updated in real time (every packet).
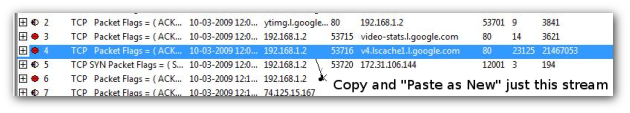
2. Locate the TCP Stream carrying FLV traffic. These are typically the really large ones. Select the stream, copy the stream (Edit->Copy) and Paste it as a new file (Edit -> Paste as New). Voila ! Switch to the User Objects in the new file and you will find the FLV without all the other clutter.
Script the whole thing using Ruby
The right clicking novelty quickly wears out after a while. You really want to automate this type of forensic stuff.
Here is a sample which shows you how you can use Ruby to script this stuff.
Task : Extract all the videos in a capture file as separate playable files. (including the ones that were aborted in the middle due to the use losing interest)
1. Save the capture as USNF format (this is the scriptable format used by Unsniff).
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
# # extract FLVs from a capture file (USNF format) into a directory # require 'win32ole' raise "Usage : xu2be <capture-file>" unless ARGV.length==1 UnsniffDB = WIN32OLE.new("Unsniff.Database") UnsniffDB.OpenForRead(ARGV[0]) UOIndex = UnsniffDB.UserObjectsIndex (UOIndex.Count-1).times do |idx| uo = UOIndex.Item(idx) if uo.Type == 'FLV' uo.SaveToFile("Video_#{idx}.flv") print "Saved file Video_#{idx}.flv\n" end end UnsniffDB.Close |
2. Run this script like so
|
1 2 3 4 |
C:\vboxshare\CAPS>ruby xu2be.rb incomplete-youtube.usnf Saved file Video_91.flv Saved file Video_192.flv Saved file Video_193.flv |
We are still working on tweaking the experience for our upcoming Unsniff 2.0 release. In the meantime, we invite you to try out the Unsniff Beta 1.8 and give us feedback on what you’d like to really see.