We have to take a small detour into Linux land and leave the comforts of the Visual Studio family. The reason : we are developing a small yet powerful remote analysis station for the upcoming release of Unsniff that can run on a commodity appliance. (Details later)
So, I cleaned out a box (AMD x2 64-bit, Fedora 7) and decided to find me the IDE I wanted. The candidates were :
Eclipse
First, lets write off Eclipse. There were some posts on the internet claiming that if you replaced the Linux JVM with a new one from Sun, things would be faster. Call me irrational but I cannot accept any latency while coding.
KDevelop
This won the best Linux IDE award organized by Linux New Media. So, I installed this one. It was quite impressive. The only problem was that it crashed when you typed something in the editor. I tried turning Word Complete off in both Settings->Configure KDevelop and Project->Options->C++. It still crashed. I had no energy to carry on given that Code Completion was one of my main requirements.
Anjuta
This one seems good, but I was simply unable to install it. I installed all the dependencies by hand, but I simply could not find these two packages
No package ‘gdl-1.0’ found
No package ‘gdl-gnome-1.0’ found
I will probably revisit Anjuta later. I was also quite amazed to find that its lead developer happens to be an Indian by the name of Naba Kumar. This would certainly make him the biggest Indian contributor to open source. Sidenote : Why dont we ever hear about these guys in the tech media ?
OpenLDev
After running out of steam, this was a desperate attempt to find something. This installed fine, but the functionality was very minimal. The editor was also the stock gEdit.
I know I could probably get any of the above working if I spent time scrounging the internet for help. I decided instead to beef up vi to make it suitable for C++ development.
How to use vi for C++ development
Here are some tips to soup up your vi for C++ development. I hope someone will find this useful.
1. First update to the latest vim. As root type “yum update vim”
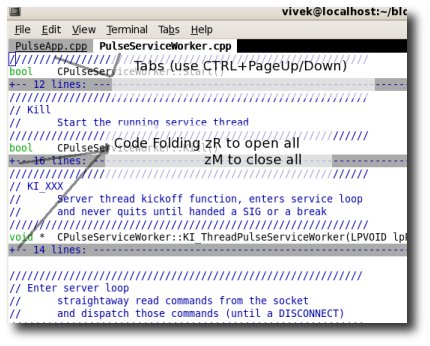
2. Enable code folding, add these lines in your $HOME/.vimrc
set fmr={,}
set fdm=marker
Now vi will fold your C++ code as shown in the screenshot, you can use the keystroke zR (to open all folds) or zM (to close them all). Use help for other options.
3. Map a key to switch between C++ source (the CPP) and the Header (the H) file.
Add the following line to $HOME/.vimrc
map :p:s,.h$,.X123X,:s,.cpp$,.h,:s,.X123X$,.cpp,
Now you can simply press F4 to toggle between the header and source file.
4. Install an excellent set of scripts called C.VIM available from
This script adds a TON of features such as automatic comment blocks, blockquote templates, and much more. This only works with gVim the graphical version of vim.
5. Use vim tabbed editing.
Yes, you can open files in new tabs even in the terminal mode of vim. Do do so, use
:tabe filename.h
To switch between tabs, press Ctrl+Page Dn / Up
6. Use sessions to save all your tabs and file editing positions.
It will save you a ton of time while resuming work the next day. To use this feature :
Type :mks! whenever you want to save the current state of open windows, cursor positions, etc.This will save your current vim session, including all tab windows into a file called Session.vim. Next time you start type vim -S Session.vim. Voila, you are back to exactly where you left off.
To faciliate this I aliased the session command via:
alias svi=’vim -S Session.vim’
7. Using code completion. Vim has support for code completion.
Although not as good as VS (especially with Visual Assist – which we use for Windows Development) – this is very fast and almost good enough. To use this :
Type part of a word and press Ctrl+P. You will be presented a list of options, keep typing or select one of the options.’
So, for now we will continue to use vi for C++ development. Until we have some spare time to investigate Anjuta or get KDevelop to stop crashing.
Â
[tags] vi, vim, C++, KDevelop, Anjuta [/tags]
Â