We just enhanced the SSL/TLS capabilities of Unsniff Network Analyzer substantially in our newest release (1.8.0.1420)
- Support for TLS extensions – RFC 4366
- Support for TLS extensions – RFC 4492 (ec_point_formats and elliptic_curves)
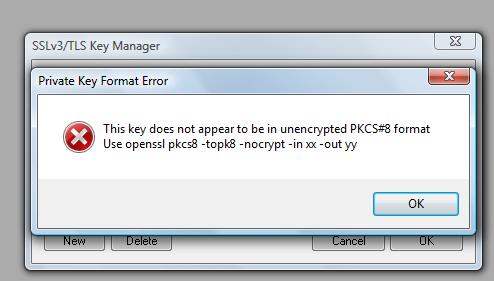
- Validates if specified key file is in unencrypted PKCS#8 format
- Support for the latest TLS extension Renegotiation_Info with the tentative extension number of 0xFF01. This is the fix for the TLS MITM Renegotiation Flaw that has been making the rounds the past couple of weeks. See the Internet Draft at http://tools.ietf.org/html/draft-rescorla-tls-renegotiation-00
In this release :
Verify if the specified key file is unencrypted PKCS#8
This is the number one problem people face when using Unsniff for decrypting SSL/TLS. The private key needs to be in unencrypted PKCS#8 format. Prior versions of Unsniff happily allowed you to specify a key in any format, but would log an error message “Invalid Key Material …..” when the time comes to use it.
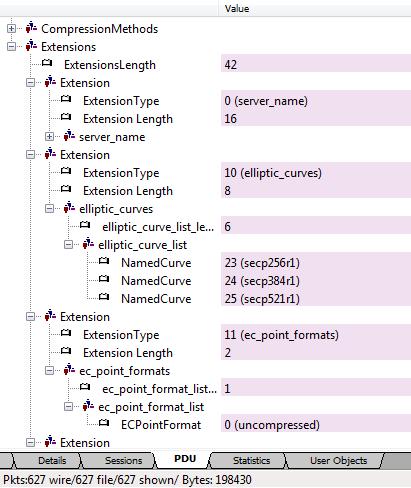
TLS Extensions
Here is a screenshot of Unsniff’s support for TLS extensions. Most but not all extensions are completely decoded (not just shown as TLV blobs Type-Length-Value).
But we already have Wireshark
We all use and love Wireshark. But if you work with SSL/TLS a LOT then you need to give Unsniff Network Analyzer a try. It could be useful to have it around in your toolbox along with Wireshark. Specifically, Unsniff could save you bunch of time because (1) it can produce bounce diagrams that you otherwise need to draw by hand (2) it can reassemble upper layer content like web pages (3) it tracks entire SSL records not just ethernet link layer packets (4) scriptable using Ruby (5) share decrypted packet captures without sharing the private keys.