I’d like to illustrate how reassembly/reconstruction can give an investigator the much needed “entry points” into analyzing a dump of packets.
The demo test case is the Forensics Challenge #4 published by the good guys over at Honeynet.org https://www.honeynet.org/challenges/2010_4_voip You have to answer the challenge yourself of course.
1. Just got a dump of packets, now what ?
Most of us would load the thing into Wireshark and see if we can get some clues. While this gives you the best available protocol breakout of every link layer packet, it could be overwhelming. An alternative and potentially more efficient approach is to look at higher layer data first and identity “entry points”. You can then follow these entry points all the way down to bit level protocol decodes. Two such higher layers are content and flows.
2. Content and Flows
Content like images, video, voice calls, HTML pages, are meant for humans while fragmented TCP packets are not. So, a good place for a human analyst to start is to see if the network analysis tool was able to reconstruct content. If you can see the images, web pages viewed, files transferred, hear voice calls, you can get a fair idea of what the dump contains. You should keep in mind the limitations of the tool and the lurking party pooper (encryption).
Another key starting point is flows. It helps you identify the ones with high volumes in a noisy environment. An example : A typical YouTube video view involves dozens of tiny flows and one huge flow that contains the video being viewed.
3. Example : Forensics Challenge #4
Lets import the Forensics Challenge data pcap into Unsniff Network Analyzer. Unsniff gives you the following levels of reassembly as first class objects (just like packets).
- Raw link layer packets (like Wireshark)
- Reassembled PDUs
- Flows
- Content (known as User Objects)
- Basic Statistics
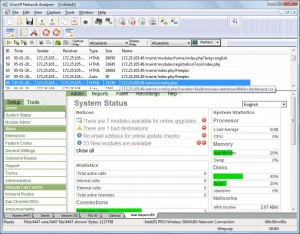
Import the pcap and switch over to the User Objects sheet.
You will see a bunch of HTML/Images/VoIP calls. Clicking on a HTML object renders the page as it was viewed. To reconstruct the HTML you have to enable the option as shown here.
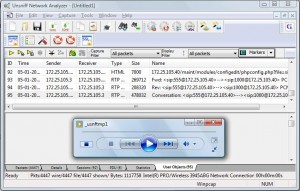
Right click the VoIP calls to check if the call is worthy of packet level analysis.
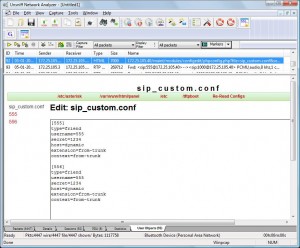
View form being edited
Conclusion
By starting off at the top layer (content), we know right off the bat that we are dealing with a Trixbox admin session and a VoIP conversation. We know all the pages on the Trixbox server which were visited / edited and the actual VoIP call that took place. With this context firmly in place we can dive down to the flow level and then to the packet level with a much better understanding of what we are dealing with.
Getting this context would have been time consuming if you started your analysis from the bottom, link layer packets.
——-
You can download and try Unsniff Network Analyzer. It can be your perfect Wireshark complement.
You may also want to try out our upcoming product Trisul Network Metering and Forensics. A Linux based 24×7 surveillance system designed for Network Security Monitoring.