Trisul meters network traffic, extracts flows, resources, and contains a powerful raw packet index. While this is a very powerful feature set for monitoring and retro analysis purposes, it would be great to correlate all of these with security alerts. You can arrange for Trisul to pick up security alerts generated by Snort or Suricata from a Unix socket .
This guide below explains how to set it up :
How to configure Snort and Suricata to send IDS alerts to Trisul
What it gives you
Here are some screenshots from processing about 40 million packets from the Defcon 17 trace set.
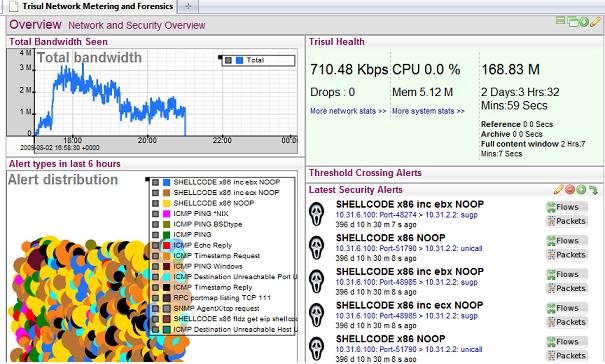
Dashboard view :
- add alert widgets to any traffic or flow dashboard
- click on Packets to get relevant packets that caused the alert in tcpdump format
- click on Flows to get the flow the caused the alert and also “nearby related” flows
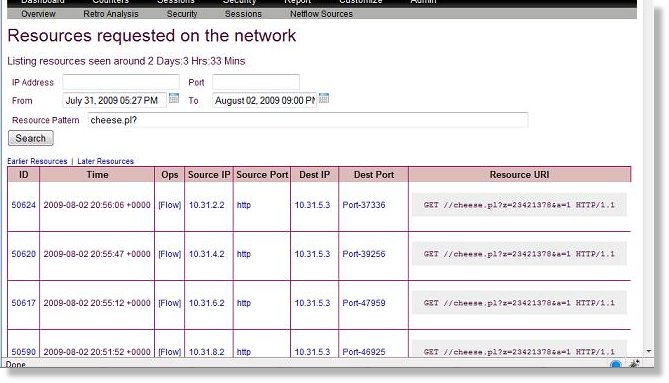
Resource view
This features is available even without Snort/Suricata but is worth mentioning in this context.
- Trisul reassembles TCP flows (even those hopelessly fragmented) and pulls out resources requested. These correspond to services. The only resource type supported now is HTTP URLs
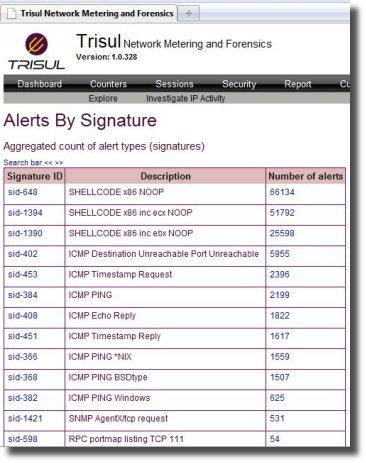
Aggregated alerts
You can view aggregated alerts for any period of time.
Performance Tip
The approach here does have a drawback in that both Suricata/Snort and Trisul look at the packet data. This is not optimal from a performance viewpoint as the same data takes on two lives in the cache. Due to GPL licensing issues, Trisul cannot simply “call out” to these two products while the cache is still hot. On fast networks (above 500Mbps) you may want to add a couple of extra cores and pin Suricata/Snort to those cores.
If you have CentOS 5.3 or above 64-bit you can download Trisul today. The trial is full featured but only retains a 3-day window of data.