We’ve written how EDH (Ephemeral Diffie Hellman) offers perfect forward secrecy in the sense that if even if you got your hands on some keying material such as a private key file, you cant decrypt past captured traffic. With DHE, what’s done is done, baby.
But.
A post on the Wireshark Q&A site wondered if you controlled the client or the server and could output the so called master secret, can you then decrypt the SSL/TLS traffic? The answer is absolutely!
If you had the master secret, it does not matter what key exchange algorithm you use. The only question left is : Do you support decryption of the cipher!
Differences with Wireshark
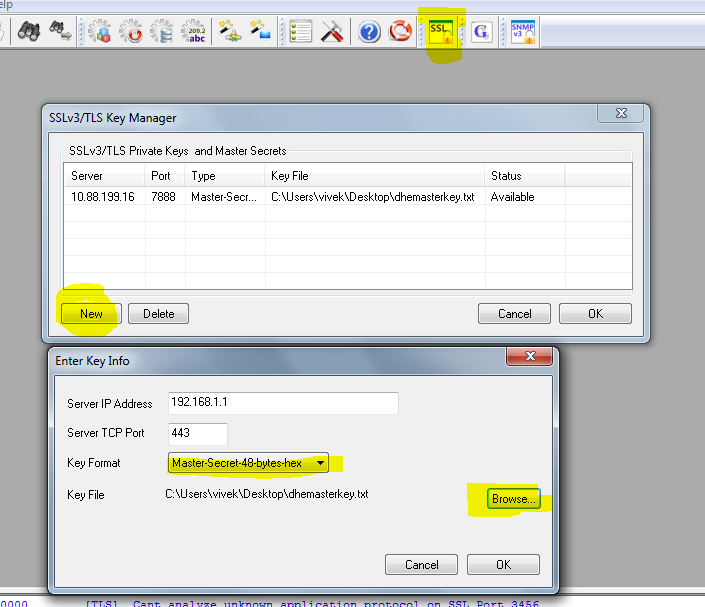
Unsniff supports entering a master secret directly. Wireshark allows you to enter something called a ‘unencrypted pre master secret’, we think if you can instrument the client anyway – why not just print out the master secret. Unsniff also doesnt care about the session id as a way of mapping flows to keys – the mapping is much weaker. You can arrange to split your PCAPs into flows -> key mapping instead.
Sample run with ECDHE-RSA-RC4-128-SHA (what gmail prefers)
Use the s_client tool to generate a trace run by connecting and typing “GET /”
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 |
dhinesh@dhinesh-System-dev:~$ openssl s_client -host gmail.com -port 443 CONNECTED(00000003) depth=1 C = US, O = Google Inc, CN = Google Internet Authority verify error:num=20:unable to get local issuer certificate .. --- No client certificate CA names sent --- SSL handshake has read 2110 bytes and written 348 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-RC4-SHA Server public key is 1024 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE SSL-Session: Protocol : TLSv1.1 Cipher : ECDHE-RSA-RC4-SHA Session-ID: 19AA250D4CF5142DB5E6FCEF07738070F6B0977647BF8C32EC1B75CC85A4FC3D Session-ID-ctx: <strong> Master-Key: 05FCDE36BE947C1A8981F0F400524C57DB632B323F144A87A2F73FC258E8AC032EE06DB36B9D3C68C3C7621E8AEC7601</strong> Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 100800 (seconds) TLS session ticket: 0000 - eb 3e 92 dc ef ab dd 75-1f 2b ce 7e 22 58 99 94 .>.....u.+.~"X.. --- GET / HTTP/1.0 302 Found Location: https://www.google.co.in/ Cache-Control: private Content-Type: text/html; charset=UTF-8 Content-Length: 222 X-XSS-Protection: 1; mode=block X-Frame-Options: SAMEORIGIN .. <HTML><HEAD><meta http-equiv="content-type" content="text/html;charset=utf-8"> |
Notice that big string in bold. That is called the master secret. That’s all you need.
If you have Trisul running in your egress point, grab a PCAP of the above session. Or alternatively run a tcpdump before the s_client tool.
Enter the master secret
Self evident, just use the highlighted buttons.
Run Unsniff on the PCAP
If you clicked on Pull Packets in Trisul, it will automatically open Unsniff the run the decryption for you. Alternately, load the PCAP into Unsniff via File -> Import -> From Libpcap
PDUs
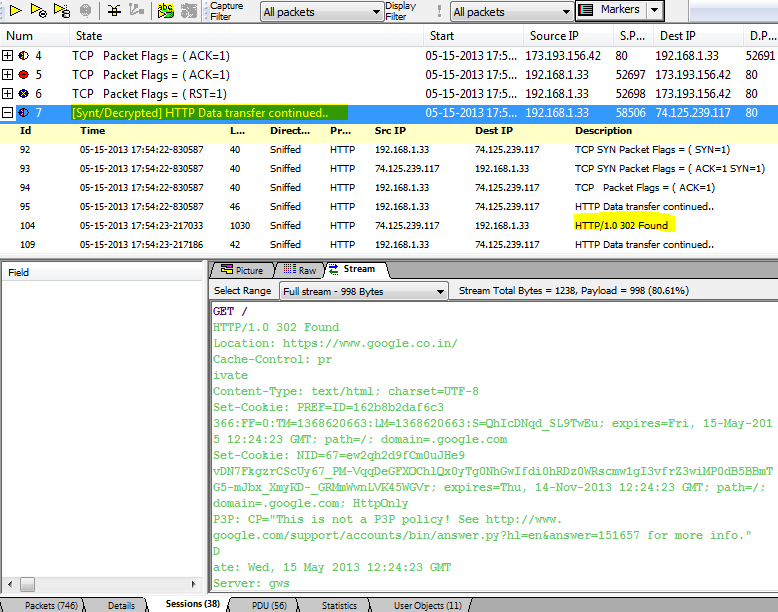
The place to observe the action in Unsniff is in the PDU tab. This may be a little confusing for folks familiar with Wireshark’s link packet based views. What Unsniff does it shows you complete SSL “records” – so an Application Data encrypted record maps cleanly into a “decrypted” record. This is shown with an icon on the left side.

Stream based view
Switch to the streams tab for two extra streams generated from the SSL stream.
- Decrypted stream stopping at the TCP layer
- Decrypted stream going all the way to the HTTPS (or whatever else) layer
Unsniff is still heavily developed
We’ve received a bunch of emails asking about Unsniff. We are still heavily improving it, unfortunately the documentation and new website is still some time off due to our big Trisul releases. The latest versions for example have top notch reconstruction – even of Video Chats with playback of VP8 and MPEG4-TS, unidirectional streams from satellite connections and more. Check it out now.
I did this exact same steps, nothing got decoded.
– ran tcpdump
– started s_client to 74.125.239.146 (www.google.com)
saw the master key in the output
sent the request GET / HTTP/1.1
got the HTML response
– stopped s_client and tcpdump
– create the master key in unsniff & imported the pcap file
– nothing got decoded – still seeing as “application data”
I tried with –cipher ECDHE-RSA-RC4-SHA option also – same problem