I stumbled across this post on “behindthefirewalls.com” blog about the recent PHP.com compromise titled “Extracting files from network traffic capture“. In that blog, the author has demonstrated file carving using Wireshark and other tools.
There is also a link to a Barracuda PCAP file (1.3MB) contains some malware http://barracudalabs.com/downloads/5f810408ddbbd6d349b4be4766f41a37.pcap
I’d like to introduce you to Unsniff Network Analyzer‘s nifty file extraction that addresses the following issues in the PCAP.
- The EXEs are transferred as content type “text/html”
- All files have to be written to disk before you can do a file * and pick out the EXEs
The latest version of Unsniff has two extremely useful features that can really speed up this process. Each User Object now has two new attributes
- Magic String : We take the first 4 bytes of each content and create a human readable string
- MD5 Hash : Each user object has a MD5 content hash
These are computed online as traffic is being processed. Once they are stored in an Unsniff Capture File Format (*.USNF) you can just access them instantaneously without reprocessing.
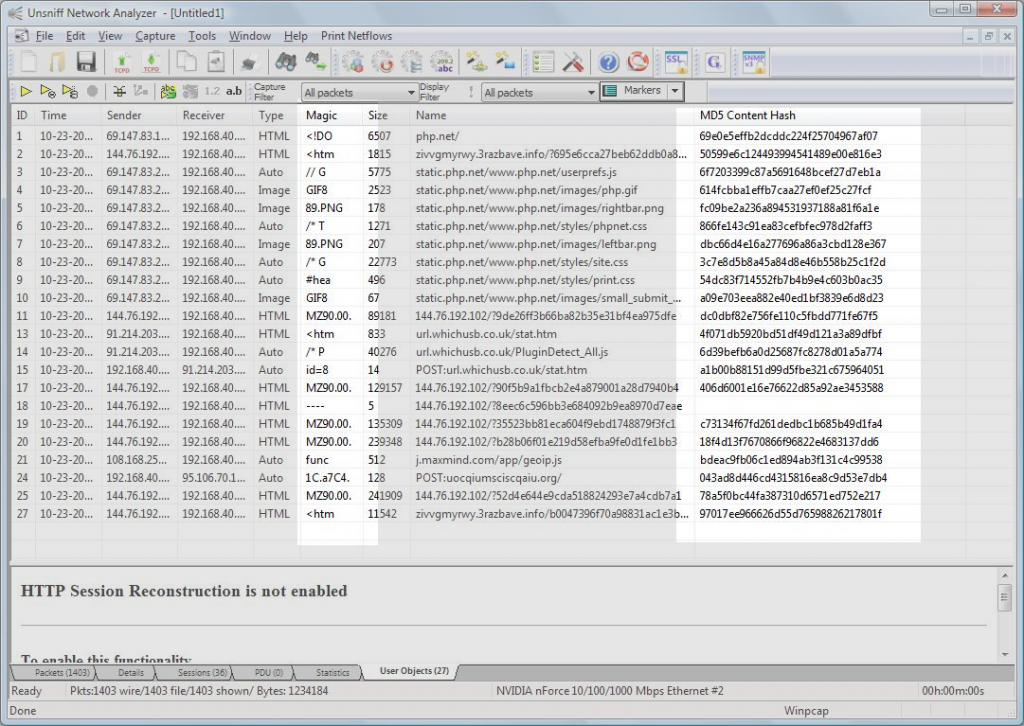
Magic number – pick out EXE transferred as text/html
As mentioned, the Barracuda PCAP drops EXE malware as text/html. In the screenshot below, If you notice User Object 11 – the Type column shows “HTML” but the Magic column shows “MZ90.00.” Thats a dead giveaway that the content isnt really HTML. Next, you can click on the corresponding MD5 column to start checking with VirusTotal etc.
Files like CSS/JS/HTML usually just have the first 4 bytes of text as the magic number. You can simply ignore them. The best part is this feature works for all files transferred – whether as EMAIL attachment, as FTP files, as Chat file transfers, etc, etc.
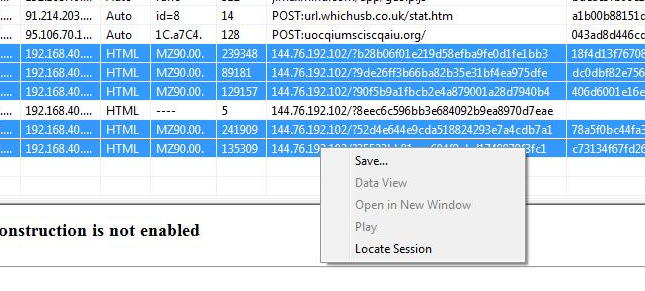
Saving all the Malware EXE files
The way you save the malware files is to simply “Ctrl-Click” and select all those who start with the EXE Magic number. Then Right Click and Save.
What gives Unsniff even more power is that the entire process above is scriptable in Ruby or VBScript. You never have to open a single GUI window. You can use the Unsniff Scripting API to automatically chew through PCAPS and continuously dump only the EXE files this way.
If you are into info sec, Unsniff Network Analyzer is a tool that you really need to have in your kit. Download for free today.
Do you handle extraction from HTTP tcp streams that has been gziped or chunked?
Sorry for the late reply.
Yes we support GZIP and CHUNKED responses too.