Thanks to a user request, we just released a new build of Unbrowse SNMP with some advanced SNMPv3 features. Now, you can –
- Run an authentication check on all SNMPv3 traps
- Work as a “normal” trap receiver (see end of post)
Why authenticate ?
Out of the box, Unbrowse SNMP will show you all traps that fly past it. It does not care if the traps are ‘real’ or ‘forged’. This allows you to see all trap activity on the network. While, this behavior is favored in a large number of cases, sometimes you want to flag them as being authentic or not.
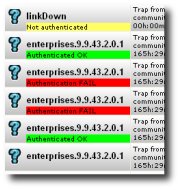 |
Yellow – Not authenticated (You must enter the required passphrases for the agent + username)Â Â
Green – Authenticated OK Red – Authentication FAIL (The signatures dont match, you can get some more detail in the details window) The auth check is not run for noAuthNoPriv and SNMPv2 traps. |
How this works ?
When the authentication check is turned on, a HMAC signature is calculated for each received trap. This computation is based on the authentication protocol (MD5/SHA), and auth password available with Unbrowse SNMP. If the computed signature matches the one carried in the trap message, we declare the trap authenticated.
Â
Using the feature
- First enable this feature via Tools->Customize->Authenticate Incoming Traps.
- Enter agent information IP address, user name, auth protocol, and auth password using Agents->Manage
- Run the trap receiver as usual. Unbrowse will now run an auth check for all agents + users for which it has the required passphrases available.
For advanced users
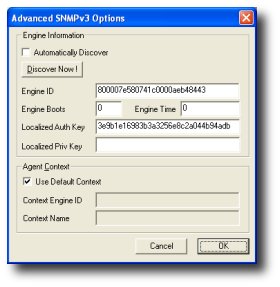
A major part of running the authentication check is the key localization algorithm. This is the process of converting a pass phrase to a key that is unique for every engine ID. You can speed things up by having Unbrowse SNMP use the key instead of the passphrase.
To do this :
- Open the Agent Manager via Agent->Manage
- Enter name, address, and select SNMPv3
- Enter the User Name, select auth protocol, and enter the auth password
- Now click on Advanced
- Uncheck the Discover Engine ID box and click Discover Now !
Unbrowse will discover the engine ID and localize the password for that agent. See screenshot.
Now, continue to use the Trap Receiver as usual.
Operate as a normal trap receiver
First – a secret! Unbrowse is fundamentally different from other trap receivers out there – it doesnt actually listen for traps on a specific UDP port. It is designed to work as a Zero Configuration Passive Trap Receiver. What that means is that you can stick Unbrowse SNMP in front of a troublesome router or management station and immediately start seeing traps. No messy addition of trap targets.  All vendors, all boxes are supported right out of the box. You can listen to traps on many UDP ports (not just one). It makes it very easy for a network admin to plugin and plugout with ease and safety.
The downside is that if you are using Unbrowse as your primary trap receiver, then you may get an ICMP Destination Unreachable / Port Unreachable packet back. This is because no one is listening on the standard SNMP Trap port 162.
We had a user request this feature earlier (how can we see loopback traps?). So, we have added an option that makes Unbrowse SNMP listen to a UDP port, like all the rest.
To use this :
1. Go to Tools – Customize – Advanced – Trap Console
2. Select “Normal UDP Socket” as the Preferred Provider
If you want to change the default port 162, edit the TBCFG.xml file in %APPDATA%/Unbrowse/Cfg folder.
These are FREE FEATURES (thats right !) Download your copy of Unbrowse SNMP today.
Â
[tags] SNMP traps, SNMPv3 trap receiver, Unbrowse SNMP, authentication [/tags]